An RTP (risk treatment plan) is an essential part of an organisation's ISO 27001 implementation process, as it documents the way your organisation will respond to identified threats.
- Iso 27001 Risk Assessment Pdf
- Iso 27001 Risk Assessment Methodology
- Iso 27001 Risk Assessment Template .xls
- Iso 27001 Risk Treatment Template
- Iso 27001 Risk Register
ISO 27001 Benchmark Spreadsheet. This spreadsheet contains a list of the controls found in ISO 27001 and enables the user to benchmark intended risk treatment against an international baseline (rather than risk assessment purposes). Jul 03, 2018. ISO/IEC A.8.1.1, A.8.1.2. And operational requirements are understood and inform the management of cybersecurity risk. Risk Assessment (ID.RA): The organization understands the cybersecurity risk to organizational operations (including mission, functions, image, or reputation), organizational assets, and individuals.
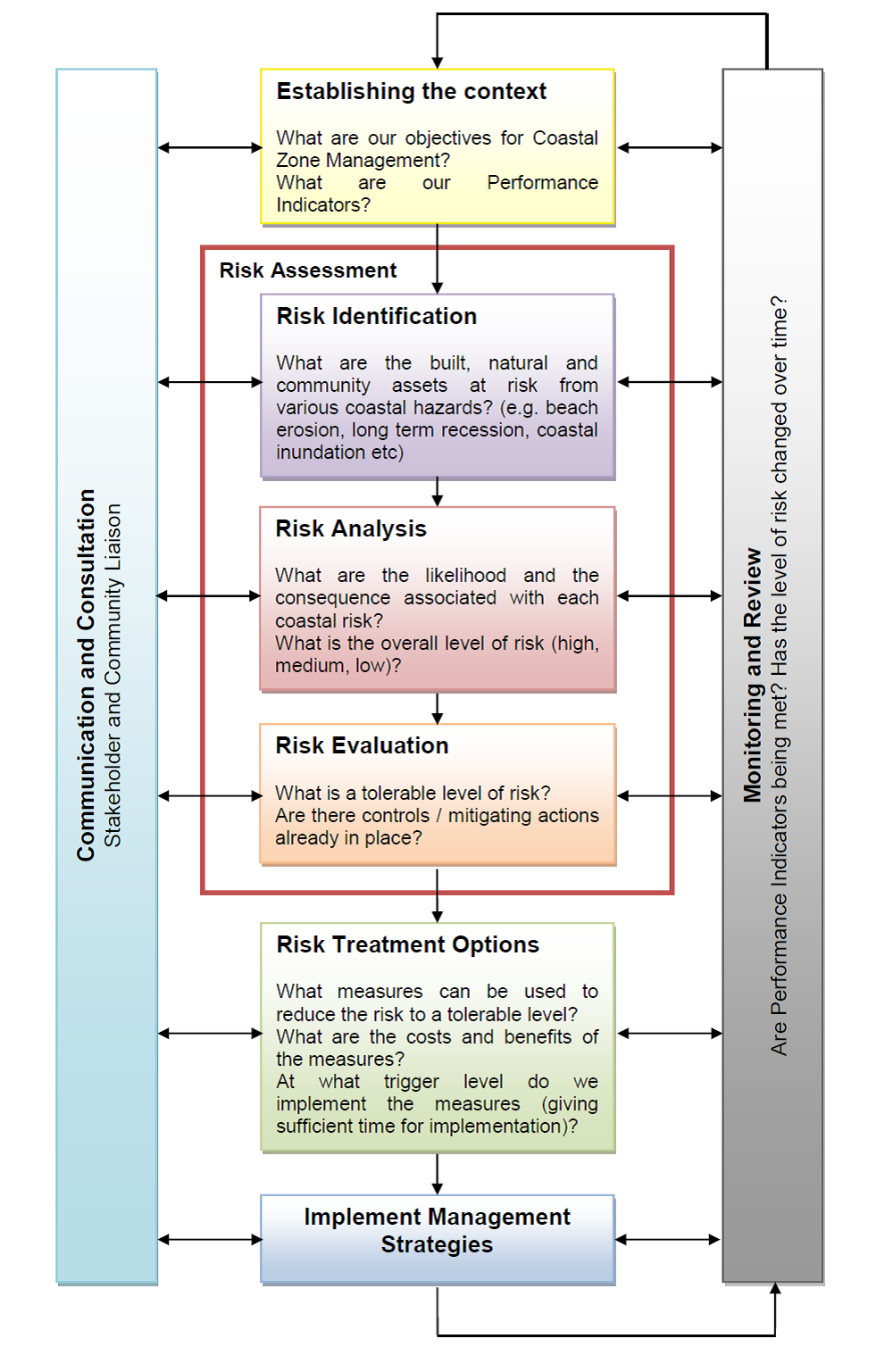
It's one of the mandatory documents you must complete as part of your ISO 27001 implementation project, and forms the final stage of the risk assessment process.
What are your risk treatment options?
Once you've completed your risk assessment and defined your risk appetite, you'll be left with a list of ‘unacceptable' threats that need to be addressed.
ISO 27001 recommends that organisations take one of four actions:
- Modify the risk by implementing a control to reduce the likelihood of it occurring. For example, you might address the risk of a work-issued laptop being stolen by creating a policy that instructs employees to keep devices with them and to store them safely.
- Avoid the risk by ceasing any activity that creates it. This response is appropriate if the risk is too big to manage with a security control. For example, if you're not willing to take any chances of a laptop being stolen, you might choose to ban employees from using them outside the premises. This option will make things less convenient for your employees but will drastically improve your security posture.
- Share the risk with a third party. There are two ways you can do this: by outsourcing the security efforts to another organisation or by purchasing cyber insurance to ensure you have the funds to respond appropriately in the event of a disaster. Neither option is ideal, because you are ultimately responsible for your organisation's security, but they might be the best solutions if you lack the resources to tackle the risk.
- Retain the risk. This option means that your organisation accepts the risk and believes that the cost of treating it is greater than the damage that it would cause.
Selecting appropriate controls
The most common risk treatment option is to modify the risk, because it typically offers the best combination of security and cost.
Organisations can determine the best way to modify a risk by looking at the controls listed in Annex A of ISO 27001. It lists 114 controls, which are split into 14 sections (or ‘control sets'), each one tailored to a specific aspect of information security:
- Information security policies: how policies are written and reviewed.
- Organisation of information security: the assignment of responsibilities for specific tasks.
- Human resource security: ensuring that employees understand their responsibilities prior to employment and once they've left or changed roles.
- Asset management: identifying information assets and defining appropriate protection responsibilities.
- Access control: ensuring that employees can only view information that's relevant to their job role.
- Cryptography: the encryption and key management of sensitive information.
- Physical and environmental security: securing the organisation's premises and equipment.
- Operations security: ensuring that information processing facilities are secure.
- Communications security: how to protect information in networks.
- System acquisition, development and maintenance: ensuring that information security is a central part of the organisation's systems.
- Supplier relationships: the agreements to include in contracts with third parties, and how to measure whether those agreements are being kept.
- Information security incident management: how to report disruptions and breaches, and who is responsible for certain activities.
- Information security aspects of business continuity management: how to address business disruptions.
- Compliance: how to identify the laws and regulations that apply to your organisation.
Deciding which control to use is relatively straightforward. The ISO 27001 implementation team should meet with a senior employee from the relevant department to agree on the appropriate control.
For example, communications security issues should be discussed with IT, staff awareness issues with HR, and supplier relations which whichever department the third party is working with.
Iso 27001 Risk Assessment Pdf
As with all major security decisions, you should run your decisions past senior management.
Once you've finalised which controls you should use, you should refer to ISO 27002 to learn more about implementing them.
vsRisk Cloud
Looking for help with you ISO 27001 risk assessment process? Take a look at vsRisk Cloud, the online version of our simple risk assessment tool.
With vsRisk Cloud, you'll get repeatable, consistent assessments year after year. Its integrated risk, vulnerability and threat database eliminates the need to compile a list of risks, and the built-in controls helps you comply with multiple frameworks, including the GDPR (General Data Protection Regulation).
Before you begin
It's worth remembering that your RTP must be appropriate to your organisation. Implementing controls takes time, effort and money, so you need to pick your battles carefully.
Iso 27001 Risk Assessment Methodology
You almost certainly won't have the resources to apply controls to every risk, even if they are small controls, such as a new process or policy.
Iso 27001 Risk Assessment Template .xls
Even a new policy requires a team of people to write and approve it, generate awareness among employees and ensure that the rules are being followed and working as intended. Latest spyhunter 4 full version crack 2016 free and torrent.
That's not to say you should abandon a control if you think that it will be expensive to implement and maintain. However, you should constantly assess whether there's a less expensive control that could generate similar results.
Iso 27001 Risk Treatment Template
Help with creating your risk treatment plan
Below is an example of what a risk-based RTP might look like, extracted from our bestselling ISO 27001 ISMS Documentation Toolkit. The toolkit also contains an asset-based RTP template.
Iso 27001 Risk Register
Example of the risk treatment plan template included in the ISO 27001 ISMS Documentation Toolkit
Developed by expert ISO 27001 practitioners and used by more than 2,000 clients worldwide, the toolkit includes:
- A complete set of mandatory and supporting documentation templates that are easy to use, customisable and fully ISO 27001-compliant;
- Helpful gap analysis and project tools to ensure complete coverage of the Standard; and
- Direction and guidance from expert ISO 27001 practitioners.
